← Back
Keeping your SCIM groups in sync with Atlassian groups
6 Aug 2024
Managing user access and permissions effectively is crucial for any organisation using Atlassian tools like Jira or Confluence. A significant part of this task involves ensuring that user groups and permissions are up to date and consistent. One of the most common challenges in this area is keeping Atlassian default groups in sync with SCIM (System for Cross-domain Identity Management) groups.
Understanding Atlassian default groups
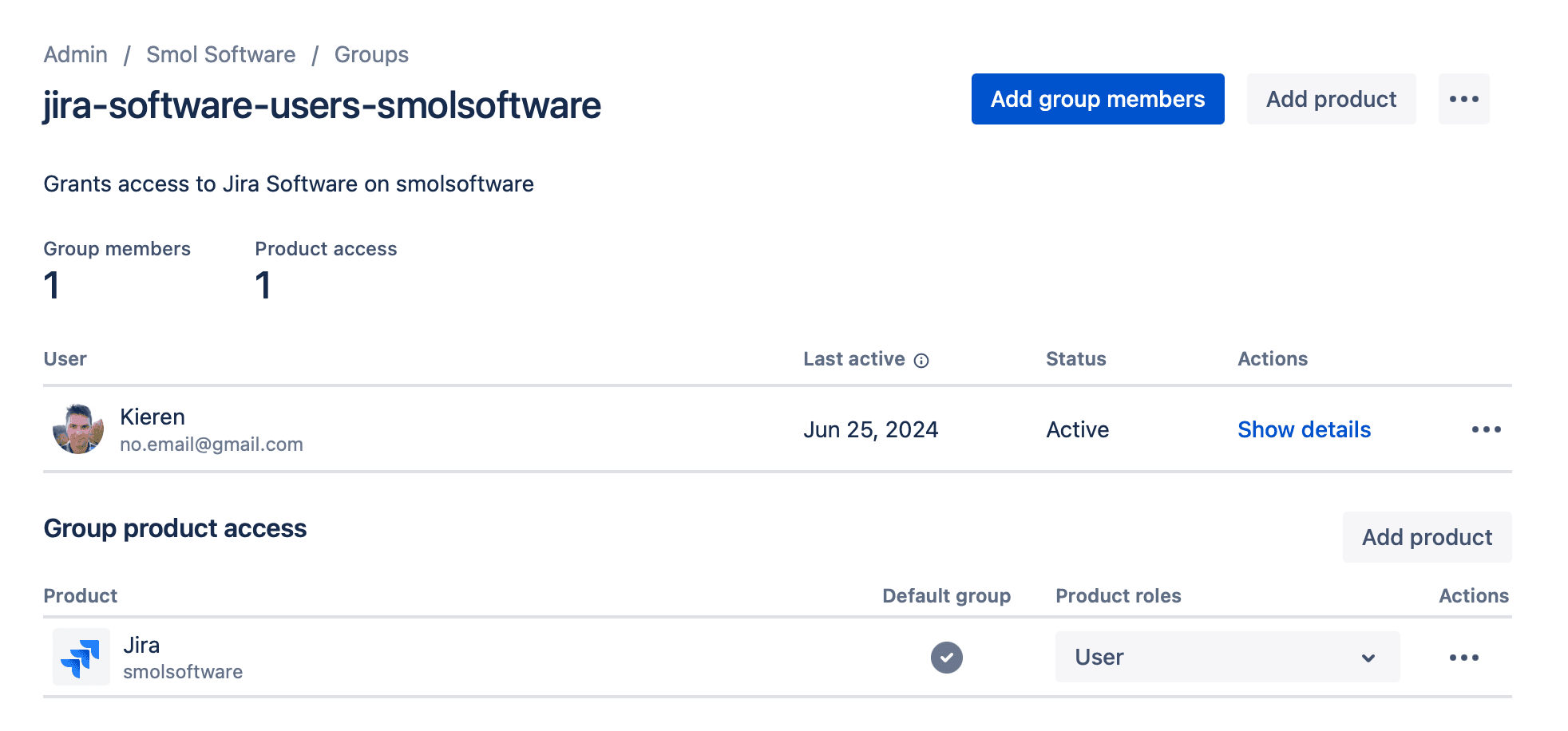
Atlassian products come with default groups such as jira-users-smolsoftware and confluence-users-smolsoftware. These groups are pre-configured to simplify user management by automatically granting product access for any user in that group. e.g. the group jira-users-smolsoftware grants the user role to Jira and the group jira-servicemanagement-customers-smolsoftware grants the customer role to users within JSM.
Any new users who are manually invited to your products (via an admin or a user) are added to these default groups to grant them product access.
More details about these default groups and their permissions can be found here.
Why synchronization with SCIM Groups is necessary
Organizations often use identity management systems to automate user provisioning and de-provisioning. SCIM is a standard protocol used for this purpose, enabling seamless communication between identity providers (IdPs) and service providers (SPs). By syncing SCIM groups with Atlassian groups, an Admin can automatically added users to groups within the Atlassian products. But, SCIM cannot sync users into the Atlassian Default groups. This means that when a user is sync’d, they will not have product access to Jira or Confluence immediately and will take longer to become an effective part of your team and organization.
How do we get around this?
There are two ways to address this issue; a long painful way and a quick way:
The long painful way is to grant your SCIM groups product access. Initially granting product access to your SCIM groups is quick and easy… But there’s a long tail end of this, where you need to ensure all your Jira projects and Confluence spaces grant users access to them via the new SCIM groups…
This means:You need to constantly ensure any new SCIM groups have the correct product access roles and are added to the appropriate Jira project permissions and Confluence space permissions.
You need to update all the existing Jira project permissions, to allow users in your SCIM groups to get access to the correct projects.
You need to update the existing default Jira project permissions, to allow users in your SCIM groups to be granted access to new projects when they’re created.
You need to update all the existing Confluence space permissions, to allow users in your SCIM groups to get access to the correct spaces.
You need to update the existing default Confluence space permissions, to allow users in your SCIM groups to be granted access to new spaces when they’re created.
The quick and easy way is to find a way to sync your SCIM groups into the Atlassian default group, that’s where our app Admin Automations comes in.
You can choose to sync any, or all of your SCIM groups into any of the Atlassian default groups.
Those default groups already grant all the appropriate product access role permissions, and they’re already setup to give users access to Jira projects and Confluence spaces.
Using Admin Automations means you get the benefits of SCIM, with none of the project or space complexities to deal with.
Your products are secure, as users have the right permissions preventing any unauthorized access.
You don’t need to maintain any manual admin processes or janky scripts to grant users product access.
Give Admin Automations a free 30 day trial now, you won't be disappointed!
In our next blog post, we’ll break down the best and most secure way to configure your groups for large organisations with a tightly locked down permission scheme.




